Researchers have uncovered a sustained and ongoing campaign by Russian spies that uses a clever phishing technique to hijack Microsoft 365 accounts belonging to a wide range of targets, researchers warned.
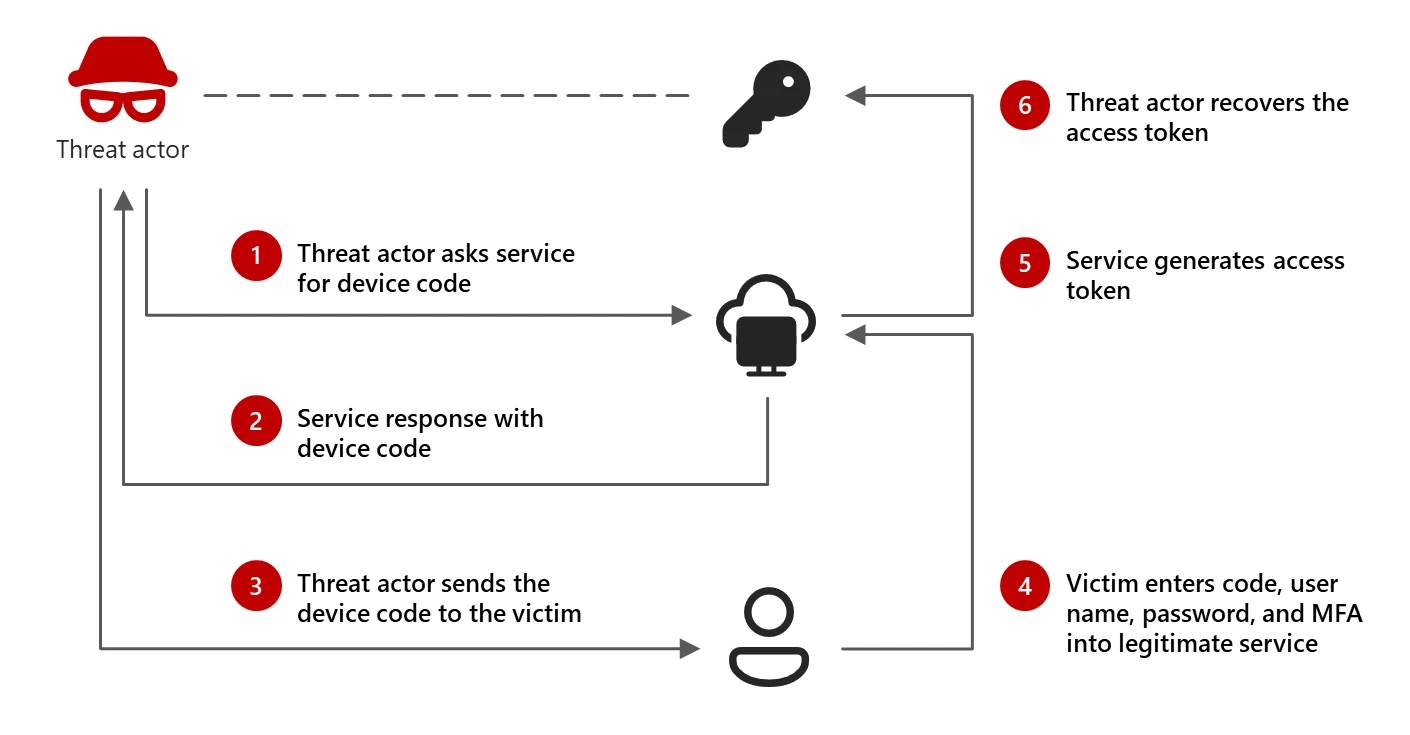
The technique is known as device code phishing. It exploits “device code flow,” a form of authentication formalized in the industry-wide OAuth standard. Authentication through device code flow is designed for logging printers, smart TVs, and similar devices into accounts. These devices typically don’t support browsers, making it difficult to sign in using more standard forms of authentication, such as entering user names, passwords, and two-factor mechanisms.
Rather than authenticating the user directly, the input-constrained device displays an alphabetic or alphanumeric device code along with a link associated with the user account. The user opens the link on a computer or other device that’s easier to sign in with and enters the code. The remote server then sends a token to the input-constrained device that logs it into the account.
Device authorization relies on two paths: one from an app or code running on the input-constrained device seeking permission to log in and the other from the browser of the device the user normally uses for signing in.
A concerted effort
Advisories from both security firm Volexity and Microsoft are warning that threat actors working on behalf of the Russian government have been abusing this flow since at least last August to take over Microsoft 365 accounts. The threat actors masquerade as trusted, high-ranking officials and initiate conversations with a targeted user on a messenger app such as Signal, WhatsApp, and Microsoft Teams. Organizations impersonated include:
- United States Department of State
- Ukrainian Ministry of Defence
- European Union Parliament
- Prominent research institutions
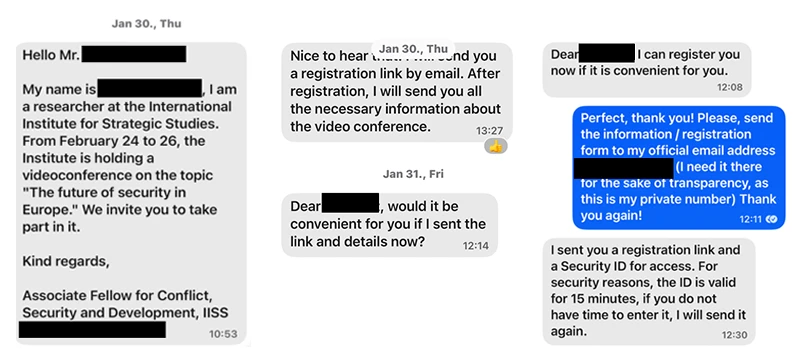
After building a rapport, the attackers ask the user to join a Microsoft Teams meeting, give access to applications and data as an external Microsoft 365 user, or join a chatroom on a secure chat application. The request includes a link to and an access code, which the threat actor generated using a device they control.
When the target visits the link with a browser authorized to access the Microsoft 365 account and enters the code, the attacker device gains access that will last as long as the authentication tokens remain valid.
“While Device Code Authentication attacks are not new, they appear to have been rarely leveraged by nation-state threat actors,” Volexity CEO Steven Adair wrote Thursday afternoon. He said that “this particular method has been far more effective than the combined effort of years of other social-engineering and spear-phishing attacks conducted by the same (or similar) threat actors. It appears that these Russian threat actors have made a concerted effort to launch several campaigns against organizations with a goal of simultaneously abusing this method before the targets catch on and implement countermeasures.”
The effectiveness of the attacks is, in large part, the result of the ambiguity in the user interface of the device code authorization process. That means it’s important for people to pay close attention to links and the pages they lead to. Microsoft Azure prompts users to confirm they’re signing into the app they expect. People should look for it and be suspicious of messages where this option is missing.
Microsoft and Volexity provide various other steps people can take to avoid falling prey to this campaign.